Sanal Kumar NJuly 8, 2024
JWT (JSON Web Token) authentication is becoming a common technique in web development and security to manage user sessions and secure APIs. JWTs offer a condensed, secure URL-based method of transferring claims between two parties.
A JSON Web Token (JWT) is an open standard (RFC 7519) for securely sending data between parties as a JSON object. This data is digitally signed, so it can be validated and trusted. JWTs can be signed with a public/private key pair (RSA or ECDSA) or a secret (using the HMAC technique).
A JWT is composed of three parts, each separated by a dot (.):
Header
Payload
Signature
1. Header
The header typically consists of two parts: the type of the token, which is JWT, and the signing algorithm being used, such as HMAC SHA256 or RSA.
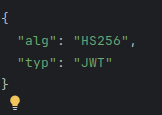
This JSON is then Base64Url encoded to form the first part of the JWT.
2. Payload
The payload contains the claims. Claims are statements about an entity (typically, the user) and additional data. There are three types of claims:
Registered claims: A set of predefined claims which are not mandatory but recommended, to provide a set of useful, interoperable claims. Some examples are iss (issuer), exp (expiration time), and sub (subject).
Public claims: These can be defined at will by those using JWTs. However, to avoid collisions, they should be defined in the IANA JSON Web Token Registry or be defined as a URI.
Private claims: Custom claims created to share information between parties that agree on using them.
An example payload might look like this:
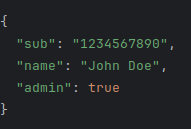
This payload is then Base64Url encoded to form the second part of the JWT.
3. Signature
To create the signature part, you have to take the encoded header, the encoded payload, a secret, the algorithm specified in the header, and sign that.
For example, if you want to use the HMAC SHA256 algorithm, the signature will be created in the following way:
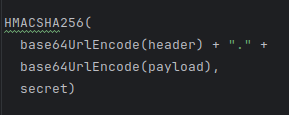
The signature is used to verify that the sender of the JWT is who it says it is and to ensure that the message wasn't changed along the way.
How JWT Authentication Works
User Authentication: The user logs in with their credentials.
Token Creation: Upon successful authentication, the server creates a JWT and sends it back to the client.
Token Storage: The client stores the JWT, typically in local storage or a cookie.
Token Transmission: For subsequent requests, the client sends the JWT in the HTTP Authorization header using the Bearer schema: Authorization: Bearer <token>.
Token Verification: The server receives the token, validates it using the secret or public key, and processes the request if the token is valid.
Advantages of JWT
Compact: JWTs are compact in size, making them ideal for use in HTTP Authorization headers or URL query parameters.
Self-contained: The payload contains all the required information about the user, avoiding the need to query the database multiple times.
Stateless: JWT authentication is stateless. The server does not need to store any session data, which makes it easy to scale.
Security Considerations
While JWTs are a powerful tool, they come with their own set of security considerations:
Secret Management: Ensure that the secret keys used for signing and verifying tokens are securely managed.
Token Expiry: Always set an expiration time (exp) to limit the lifespan of the token.
HTTPS: Always use HTTPS to protect the token from being intercepted during transmission.
Algorithm: Use strong and appropriate algorithms for signing tokens.
Conclusion
JWT authentication provides a robust, scalable, and efficient way to handle user authentication in modern web applications. By understanding its structure and working principles, developers can leverage JWT to enhance the security and performance of their applications. Whether you're building a simple web app or a complex microservices architecture, JWT can be a valuable addition to your authentication strategy.

0